这是您想要的页面.
查看搜索结果:
Choose a country or area to see content specific to your location
您希望搜索哪方面的内容?
建议的搜索
No product matches found - System Exception
符合的结果
- 是德科技主页
- 产品与服务 - 电子测试仪器
- 网络安全测试工具
- BreakingPoint QuickTest
特点
- 用户界面更简便,只需点击两三下即可执行复杂的测试例
- 一种自我稳定型目标搜索算法,用于评估各种基础设施的性能和安全性
- 持续更新的套件可确保基于互联网的当前状态实施评估
- 预先创建的问题导向式测试方法涵盖顶层性能和安全场景
- 每次运行完测试后由专家进行后期分析,得出可行的见解和建议
- 能够在同一测试平台上同时使用 BreakingPoint 和 BreakingPoint QuickTest
使用真实的应用和威胁向量验证设备和网络安全。
问题:网络安全测试颇为复杂
正确执行网络安全评估有助于详细了解网络或设备的性能,同时处理各种复杂的流量――从基础的第 2 层和第 3 层到 Web 再到复杂的应用组合(包含或不包含威胁向量)。
同样,深入的安全有效性评估需要结合使用威胁向量与逃避技术,从而准确衡量基础设施探测、允许或拦截各类攻击的能力。 这种验证对于确保网络的高性能和安全性至关重要。
但是,许多组织没有定期开展这类评估,因为能够进行此类测试的工具过于复杂,网络配置的更改也过于频繁,还有可能是缺乏具备足够知识、能够分析测试结果的员工。
解决方案:能够加速测试、缩短学习曲线的一站式测试
BreakingPoint QuickTest 根据所需测试类型提供个性化的测试方法,能够简化应用性能和安全有效性评估。 现有或近期计划推出的测试套件可提供加密性能测试、NetSecOpen、系统性能测试、周边评估和设备安全评估。
这些简单易用的测试方法充分利用了我们的全球应用和威胁情报(ATI)团队持续取得的研究结果,以及是德科技工程师在测试各种应用和安全设备以及网络方面积累的多年经验。
测试套件采用功能强大的稳定化目标搜索算法并汲取专家的分析结果,确保准确评估各种设备和系统,并在每次测试运行之后提供切实可行的见解。
BreakingPoint QuickTest 具备 BreakingPoint 的全部功能,使组织能够提高网络安全测试的速度,而不会对其他性能产生不利影响。
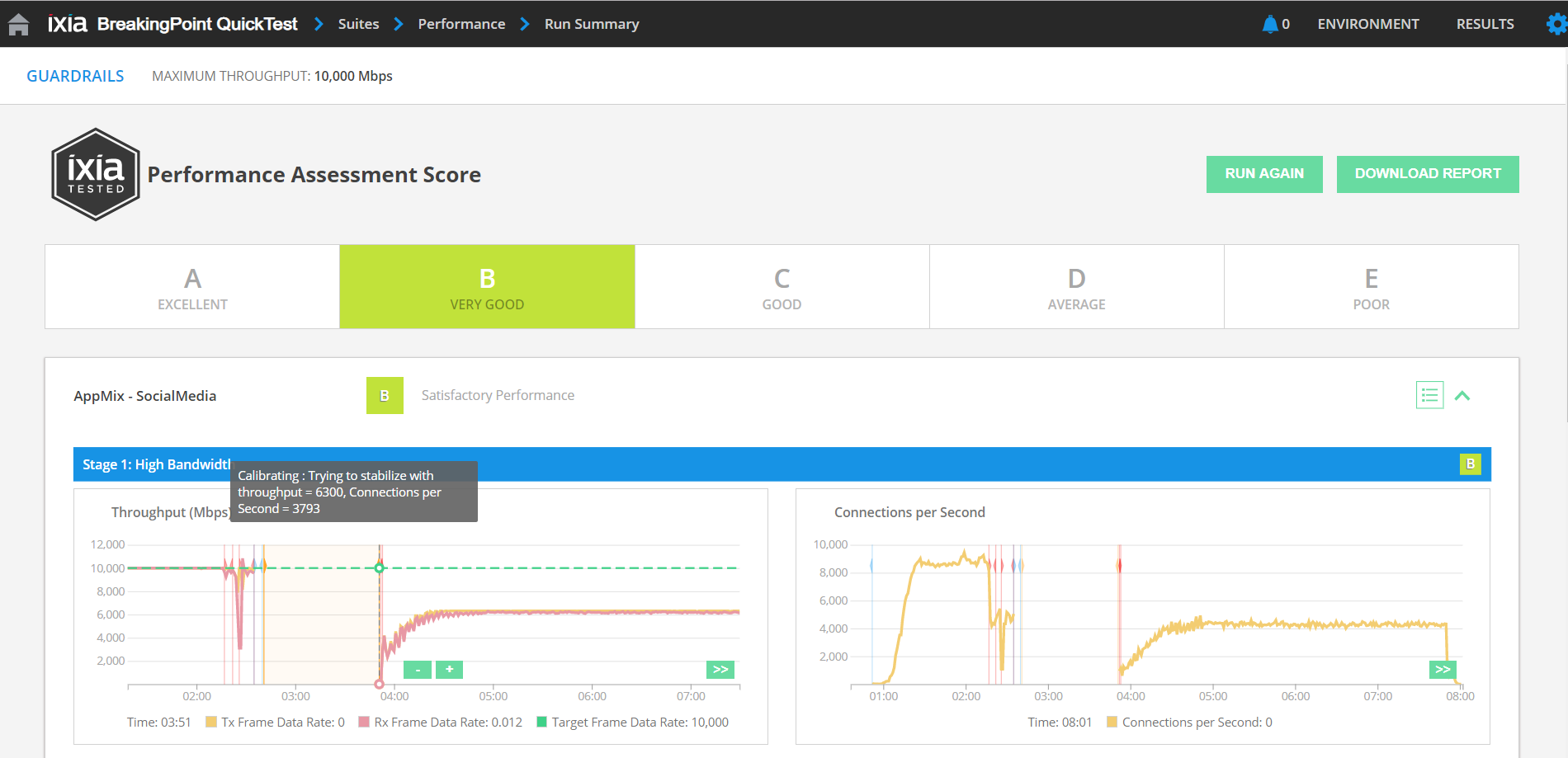
BreakingPoint QuickTest 稳定化/校准算法可以处理各种流量条件设置并找到最佳性能/安全性结果
特色资源
需要帮助或遇到问题?









 京公网安备 11010502040140 号
京公网安备 11010502040140 号